Pocket Protector®
What's Included
Pocket Protector by TetherView offers Fully Managed Email & Managed Email Protection that detects business email compromise, spam, and phishing type emails and attacks. The product catches malicious emails by utilizing computer vision, AI, 24 x 7 experts, and machine learning. Pocket Protector Managed Email Protection is fully managed and provides you with the option to either inform your users of suspicious or malicious emails through an HTML banner or block them with quarantine features. Pocket Protector adds an important layer of protection to your inbox. Pocket Protector fully manages your email to adhere with any regulatory requirements.
Phishing, Zero Day
Phishing, 3rd Party Brand Impersonation
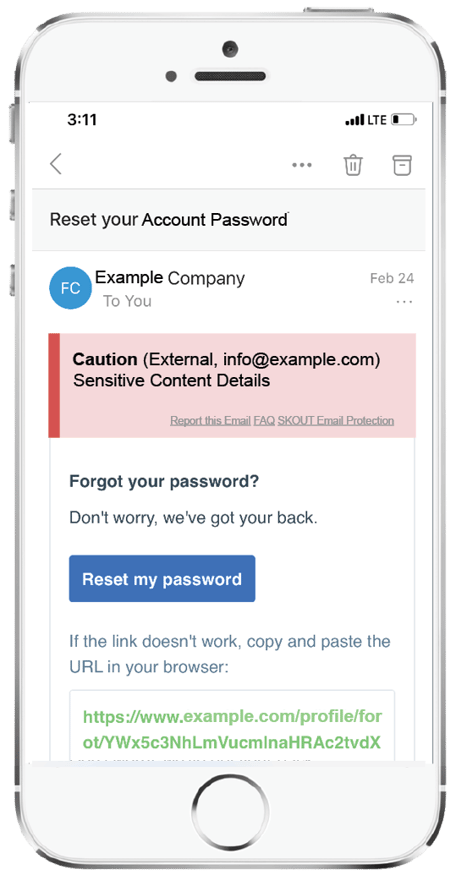
AI, machine learning, and
computer vision identify
patterns in text, image, and html
to identify potential threats. The
unique banner system allows
for borderline threats to be
flagged without compromising
business functionality
Harmful Links
All links in emails are sanitized
using a sandboxed server.
The user cannot access the
link directly. They are brought
to a landing page showing a
screenshot
VIP Impersonations
Identifies attempts to impersonate VIP's via email spoofing, typo squatting, or other tactics
Personal Device
Home Attacks
Attacks on personal devices
are mitigated by conducting
analysis on the server side and
injecting the results into the
email, completely removing the
need for remote software such
as dedicated email clients.
Dangerous Files
Scans for harmful links,
infected PDF's, and embedded
code including scripts. Analyzes
text within each email and
attachment(s) to determine if
sensitive words or phrases
are used such as: password,
invoice, payment, etc.
Malicious Insider
Machine learning develops
behavior profiles and social
graphs that identify suspicious
emails that don’t match a
known profile, triggering an
impersonation warning
AI Powered Phishing Protection for Office 365
Computer Vision
All incoming mail is automatically checked against over two dozen computer vision and text analysis models that “see” the message much like a person would; even very convincing forgeries are blocked.
Forgery Protection
Protects against both spear phishing and brand forgery attacks.
Easy Deployment
Deploys organization-wide in 1-2 hours.
Easy Deployment
The “Report Phish” link in emails would send the potential spam to our security experts. HTML sanitization blocks XSS, JavaScript, CSS attacks.
Want to know if your email platform has vulnerabilities?
Schedule a demo with us below to learn more about what makes Pocket Protector® great.


